Security and App Hardening: Five Things Management Wants to Know

Summarize with AI:
Apps aren’t just eating the world — they now underpin global business success. Consider: Almost half of users download a new mobile app every month and according to comScore, 57 percent of users’ time with digital media takes place in mobile applications. The challenge? Widely-available, highly-functional apps make ideal targets for hackers; as noted by new research from Avast, mobile cyberattacks are up 40 percent over the last year.
The result? C-suite executives and managers have tough questions for infosec pros and developers: How are you helping to prevent your critical applications from becoming an attack vector? How are your apps “worth protecting” hardened and secured? What precautions are in place to prevent compromise and limit the impact of cyberattacks?
Here’s a look at the top five things your boss wants to know about app hardening.
Our Apps Are Not Easy to Tamper With
If hackers want to breach applications, they will — but if you can make the process complicated, difficult and time-consuming many attackers will look elsewhere for easier targets. That’s the idea behind app hardening: Creating software with a security-by-design mindset that puts protection at the forefront of app design.
So it’s no surprise that your boss wants to know: How easy is it for attackers to tamper with our applications? Can hackers masquerade as legitimate users? Can they bypass critical checks to access sensitive data or alter critical code without being detected? As noted by OWASP, mobile code tampering remains a top concern for companies — if hackers can compromise existing code and convince users to download their modified version of your app, the results range from consumer identity theft and fraud to business revenue loss and reputation damage.
Here’s how to satisfy your boss: Build applications with the ability to compare current app code with approved iterations and determine if anything has been added or changed. In addition, make sure to include validation checks that aren’t standalone — access checks must include callbacks to other secure services to help verify user ID before granting approval.
We’re Compliant with all Relevant Standards
App standardization isn’t just a good idea — in many cases it’s the law. The General Data Privacy Regulation (GDPR) includes mandates around software development; as of when this legislation went live on May 25th, 2018 any application that handles the data of European Union (EU) citizens and residents must use this data with explicit consent, ensure users know what type of data is being collected and allow them to access this data upon request. Non-compliance could result in substantial fines up to four percent of global annual sales.
Other critical standards include PCI DSS, which requires companies handling credit information to both assess security vulnerabilities and assign a severity ranking. In addition, the most recent version of PCI DSS demands regular compliance checks rather than fire-and-forget security. HITRUST CSF, meanwhile, mandates that all software products undergo pre-release security assessments while the OWASP Top 10 provides resilience requirements such as the ability to detect jailbroken or rooted devices.
Bottom line? Clear standards compliance goes a long way to setting your manager’s mind at ease.
Applications Aren’t Easy to Inspect or Infiltrate
Unencrypted processes and data open the doors for hackers to infiltrate apps. Combatting this issue means more organizations are relying on sophisticated encryption to protect data at rest and in transit.
But it’s not quite so simple. Data-in-use can’t be encrypted, meaning it must be processed in the clear. And as noted by RCR Wireless, hackers are now leveraging trusted, encrypted traffic to hide malicious payloads in plain sight. The result? There’s a security gap at the application layer as hackers attempt to derail and infiltrate apps-in-use. Here, assurances to the boss active measures to prevent the production version of the app from tampering or running in a debugger or emulator. For IT pros this means solutions that not only limit the use of debuggers and remote execution to prevent code infiltration but provide post-compile visibility into critical app function. For C-suite members, this means another layer of protection: Apps aren’t easy to inspect, infiltrate or modify.
Our Apps Won’t Run on Compromised Devices
Privilege escalation remains a popular way for attackers to infiltrate devices and then ramp up their level of control. As noted by Help Net Security even Unix-based text editors are now subject to these attacks — highly complex and cloud-based mobile apps, meanwhile, are potential goldmines for malicious actors.
Here, app hardening means creating an application environment which actively detects the presence of compromised devices (rooted, jailbroken or simply infected) and prevents your app from running. In practice this means triggering real-time responses which include notifications, auto-app-exit or even permanent quarantine as required. Coding this protection from the ground up is one way to improve security but for apps already in production it’s worth considering runtime controls capable of providing real-time compromise detection and prevention.
We’re Not Giving Away Vulnerabilities
All software is vulnerable. It’s the nature of code — nothing is perfect and under the right conditions, any application can be compromised. The problem? Many companies are effectively giving away their vulnerabilities on a silver platter by providing easy ways for attackers to infiltrate apps and discover serious flaws.
The big target hardening tip here? Use basic security hygiene to keep hackers at bay. This means applying security updates ASAP (or leveraging automated tools to do the job), preventing custom SQL queries, implementing multi-factor authentication, requiring strong passwords, encrypting all sensitive information, and hardening and shielding mobile applications before you ship them. Simply put? Hackers aren’t interested in resistance, just results: Make it harder than average for them to infiltrate apps and they’ll choose another target. Before deploying an application into an untrusted environment, assess your risks and manage and protect against them.
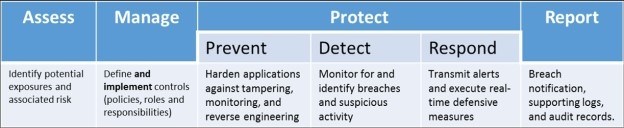
The boss is worried — what are you doing to secure critical company apps? Put the C-suites’ mind at ease by creating hard targets: Make apps tamper-proof and compliant, hard to infiltrate, quick to detect compromise and difficult to break.

Gabriel Torok
Gabriel Torok is a principal and CEO of PreEmptive Solutions, which helps companies protect the value of their software innovation and the integrity of their applications and data through a combination of binary obfuscation and application shielding. Gabriel has significant experience in software development and protection, as well as broad functional experience in operations, sales management, marketing and finance. Learn more at www.preemptive.com.
