Insecure Direct Object Reference in RadAsyncUpload
Problem
Security vulnerability CVE-2017-11357: user input is used directly by RadAsyncUpload without modification or validation.
Description
An exploit can result in arbitrary file uploads in a limited location and/or remote code execution.
Solutions
Update from Jan 5, 2021
Due to the .NET JavaScriptSerializer Deserialization (CVE-2019-18935) vulnerability, we strongly recommend upgrading to R1 2020 (version 2020.1.114) or later since the patches provided for CVE-2017-1135, CVE-2014-2217 and CVE-2017-11317 do not prevent it.
Only the upgrade to R1 2020 (2020.1.114) or later can prevent the known vulnerabilities at the time of writing.
You can find more details and instructions at Allows JavaScriptSerializer Deserialization and Blue Mockingbird Vulnerability Picks up Steam—Telerik Guidance.
Also check the FAQ section at the end of the Security article.
To ensure your application is not exposed to risk, there are several mitigation paths.The recommended approach is to upgrade to the latest version and follow the steps in the RadAsyncUpload Security article. You can find the other alternatives below.
Update from 8 Sep 2017: You should follow one of these options even if you are not using RadAsyncUpload in your application.
Update from 23 Oct 2019: Information on avoiding the issue through general web.config networking settings was removed because it is not sufficiently safe.
- Use a patch for versions between Q1 2011 (2011.1.315) and R2 2017 SP1 (2017.2.621).
- If you are on active maintenance, upgrade to R2 2017 SP2 (2017.2.711) or later.
NOTE: The patches are not available on the Telerik NuGet feed.
NOTE: If you are targeting .NET 3.5, review the FIPS Compatibility article, because the encryption issue it describes also pertains to these patches.
Use a patch for versions between Q1 2011 (2011.1.315) and R2 2017 SP1 (2017.2.621)
The R2 2017 SP2 release brings a fix and the ability to disable uploads for the first time. This fix was ported in the patches.
Download a patched version from your Telerik.com account after the 15th of August 2017. If you downloaded it earlier, download it again, because the file was updated since its original creation. Here is how to get the patch:
Go to your telerik.com account.
From the Version dropdown, select your release:
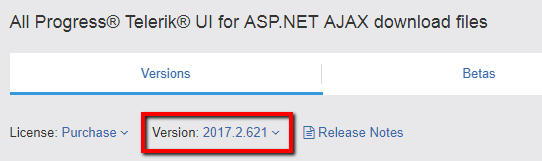
Download the SecurityPatch_<your_version>.zip file.
Replace the Telerik.Web.UI assembly in your application with the one of the same version that you just downloaded. Temporary files saved to the disk by RadAsyncUpload will now have the
.tmpextension.*(Updated on 23 Oct 2019): *Set the encryption keys described in the RadAsyncUpload Security article.
This patch brings an added security measure. After applying the patched DLL, you can now disable file uploads through the Telerik handler. To do that, set the Telerik.Web.DisableAsyncUploadHandler key in the appSettings section of your web.config to true. You can then create a custom handler with the desired level of security. If you do that, see the UploadedFiles.SaveAs Throws FileNotFound Error with Custom Handler KB article.
NOTE: Due to technical feasibility, the following versions do not have patches for this issue:
- Q1 2011 SP2 (2011.1.519)
- Q2 2011 SP1 (2011.2.915)
- Q3 2011 SP1 (2011.3.1305)
- Q1 2012 SP1 (2012.1.411)
- Q2 2012 SP2 (2012.2.912)
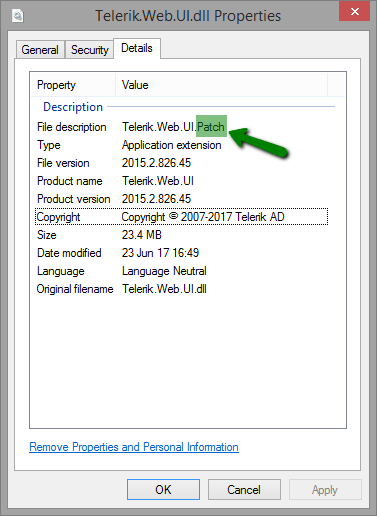
The patched version shows "Telerik.Web.UI.Patch" in the File Description under Properties in Windows Explorer:
How to spot a patched version of Telerik.Web.UI.dll:
Source code for building a patched version and protecting the Telerik.Web.UI assembly is available as well. If you downloaded it before the 15th of August 2017, you can download it again, because the file was updated.
Upgrade to R2 2017 SP2 (2017.2.711) or later if you’re on active maintenance.
- Upgrade your Telerik UI for ASP.NET AJAX versionto R2 2017 SP2 (2017.2.711) or later.
- Set the encryption keys as explained in the RadAsyncUpload Security article.
The R2 2017 SP2 (2017.2.711) release brings an additional security measure. It allows you to disable file uploads through the Telerik handler. To do that, set the Telerik.Web.DisableAsyncUploadHandler key in the appSettings section of your web.config to true. You can then create a custom handler with the desired level of security. If you do that, see the UploadedFiles.SaveAs Throws FileNotFound Error with Custom Handler KB article.
Notes
We would like to thank Paul Taylor / Foregenix Ltd and Markus Wulftange of Code White GmbH for assisting with making the information public.